Cybersecurity : Future threats and impact on electric power utility organizations and operations
This Technical Brochure offers an insight into the evolution of the cyber-physical security threat landscape for the next 20 years. The approach used is well-aligned with the concepts described for the “Grid Architecture of the Future”. Based on the guidance provided by a world-wide survey of stakeholders, the most important issues were addressed. Using a well-defined model-based system engineering process, multiple solutions were analyzed to improve the maturity posture of the technical staff and identify the spy craft tools needed for a proactive or anticipatory response to these threats.
Members
Convenor
(US)
D.K. HOLSTEIN
Secretary
(US)
T.W. CEASE
C. NEWTON (US), V. KARANTAEV (RU), W. WEBB (US), R. KING (US), T. ZHANG (CN), J.M. STORM (NO), S. NESTEROV (RU), G. ARROYO- FIGUEROA (MX), P.K. AGARWAL (IN), M. TALJAARD (ZA), J. WACK (US), C.C. LIU (US), E. MORALES (CL)
Corresponding Member : G. RASCHE (US)
Introduction
WG D2.46 built this Technical Brochure leveraging the extensive research by others – 76 references are included in the bibliography and cited in the main body text and annexes of the Technical Brochure. Working Group subject matter experts then tailored the findings of this research for EPU applications. The approach used is well-aligned with the concepts described for the “Grid Architecture” in the September/October 2019 issue of IEEE Power & Energy magazine.
Based on assessments and supporting data in existing standards, Technical Brochures, and open source documentation a portrait of the emerging threat landscape was developed for the near-term planning horizon of 10 years and for the long term of 20 years. Overlaid on this portrait was the imposition of emerging local laws and regulations. For the two planning horizons estimates of the impact on EPU cyber-physical security policies, procedures and organizational directives were derived. Each impact was then associated with recommended solutions to improve the security posture of EPU operations. For example, in the near term the architecture and capabilities needed to implement an integrated security operation centre and the technical skills of the centre’s personnel were addressed.
To guide this work, a world-wide survey was conducted to prioritize the most important issues to EPU stakeholders. Together with other general surveys found in the open literature several issues were exposed:
- Protection of mission-critical functions and their data required unique cyber-physical security skills and advanced tools such as big data analytics to detect and mitigate an attack early in the attacker’s kill chain.
- Timely response actions require new capabilities embedded in intelligent electronic devices and communication network components to provide the data needed for actionable intelligence assessments.
- Based on IEC 62443-2-4, certification of vendor cyber-physical security solutions is needed for selecting the best approach for the long term.
- Information sharing requires new technologies to ensure the protection of sensitive data while in transit or when stored in authorized repositories.
A well-defined model-based system engineering process was used to define black box and white box views of selected systems of interest. For this purpose, a commercial tool based on the Open Management Group system modelling language was selected. The tool was used to construct business process models to visualize the processes and their interactions between EPU organizations. These models were used to capture:
- The actors involved in the system of interest and the information flow among them.
- The relevance of the information to humans or device entities receiving the information
- The use of the information in terms of the action taken.
- The quality of the information needed to perform the action taken.
System model constructs were used to identify the need to satisfy specific laws and regulations. In response, it was clear that EPU policies, procedures, and organizational directives changes were needed to seamlessly integrate security and data protection into their normal operations. For example, the models expose the need for a combined role-based and attribute-based access control management plan.
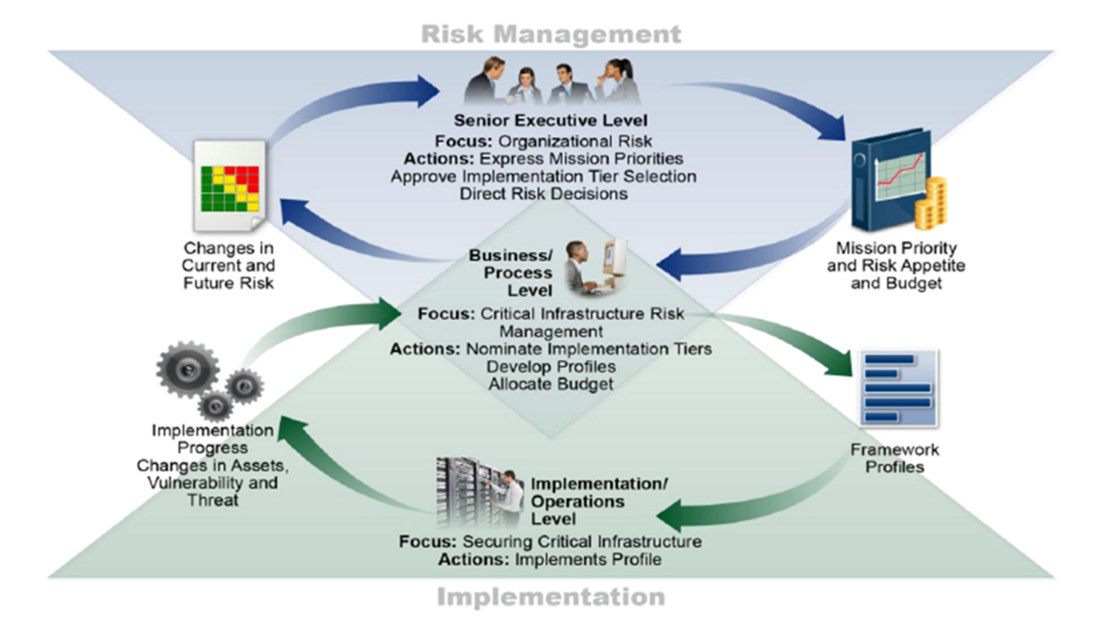
Summary of findings and recommendations
Some of the key take-way points from this work are:
- There is no standard methodology and metrics to support the projections of emerging threat, the composition of the future grid, and the interaction between them.
- Strategic cyber-physical security planning is critical for EPU’s to proactively, rather than reactively, improve their cybersecurity protection posture. Selection of the best plan and options to cope with the emerging threats, regulations, and technologies need well defined measures of success.
- Given the dynamics of the threat environment, advances in cyber-physical security solutions, and new laws and regulations, EPUs need to automate their awareness assessment process and analytics. For example, the emerging trend in attack sophistication require EPUs to develop a complete understanding of the kill chain approach and the necessity to share data with national agencies and other EPUs in a timely and secured manner.
- Most surprising from the survey response was the current EPU lack of need for vendor security certification, or more to the point vendor conformance to security standards.
This Technical Brochure identified the need for several future works:
- Develop case studies to assess the benefits and challenges for EPUs to deploy a deception-based strategy to complement an anomaly-based detection strategy. Focus attention on the strong coupling between a simplified maturity model and the kill chain model.
- Develop classes of metrics that can be used by other CIGRE study committees to quantify cyber-physical security solutions in terms of deployment rate, response rate, and degree of complexity.
- Develop a logical architecture for using cloud-based services to augment the capabilities of an integrated security operations centre.
In conclusion
This Technical Brochure offers an in-depth view of the issues, benefits, and concerns of proposed solutions that should be considered by EPU security teams. These focus on the need for improved people skills, dramatic changes to policies, procedures and organizational directives to assign responsibility and accountability for maintaining a mature security posture, and the use of advanced technologies and tools to implement a proactive or anticipatory security strategy.