Cyber Asset Management for HVDC and FACTS
CIGRE Technical Brochure 847 was developed by the Working Group B4.78 which was established in 2018. The main objectives of the WG were to provide a roadmap to address (i) HVDC/FACTS cyber security vulnerability and impacts of changing regulatory requirements, (ii) HVDC/FACTS cyber asset reduced life expectancy and replacement timelines, (iii) HVDC/FACTS cyber asset technical resource availability, training requirements, and vendor supplied continuous cyber asset security and maintenance programs and (iv) Specification of responsibilities for a HVDC/FACTS cyber security asset, divided between product vendor, system integrator, and asset owner.
Convenor
(CA)
K. WALKER
Secretary
(CA)
P. TAIAROL
P. LINDBLAD (FI), R. WENDT (DE), J. MALMSTRÖM (SE), A. HEINRICH (DE), A. KUMAR (GB), G. RAJAPPAN (US), R. TENORIO (BR), S. DO ESPIRITO SANTO (BR), M. REYNOLDS (US), S. ASHOK (US), N. KIRBY (US), P. SCHOMMER (US), D. KONG (GB)
Corresponding members: D. KELL (CA), J. AWODOLA (GB)
Introduction
The needs of the power industry are changing as technology evolves and sources of renewable energy continue to grow and penetrate the grid. Transmission using HVDC technology and the installation of FACTS will play an increasing role in the future grid. Control systems and other cyber assets for HVDC and FACTS continue to change with technological advancement and increased demands for data acquisition and monitoring. There are many benefits to this increased cyber asset functionality, such as quicker change implementation, repeatable and simplified project execution, and improved data acquisition and monitoring for asset management. However, with these benefits additional challenges can be identified in cyber security risks, the need for frequent software updates to mitigate vulnerabilities, software obsolescence, anti-virus requirements, access control, and change management in order to maintain the security of the power grid. It is important to manage these additional cyber related challenges as they may have a direct impact on the availability of the HVDC and FACTS assets.
HVDC and FACTS control and protection systems, as well as the communication network used for these systems, are unique since they are complex and typically responsible for the control of large quantities of power transmission and/or AC system stability. The control and protection systems are integrated with the HVDC and FACTS power electronic main circuit equipment and are increasingly reliant on off-the-shelf IT products and IP addressable components. Currently, a control and protection system could consist of vendor specific devices with proprietary firmware and software, combined with common ICT equipment, such as servers, network switches, workstations, routers, etc. Different parts of the control and protection system have different expected lifecycles, both from Operational Technology Cyber Security (OT-CS) and operational life-cycle perspectives. The regulatory framework applicable to implemented HVDC/FACTS control and protection systems will change during specification, design, and operational stages.
Power system cyber security requirements
The Brochure studies Cyber security requirements globally and applies these aspects specifically to HVDC/FACTS devices. Upon investigation of global requirements, key requirements common to all areas were identified. As a summary, they include:
- Cyber Asset Risk Assessment, Classification, and Identification
- Physical Security Requirements, Access Control, and Monitoring
- Electronic Security Requirements, Access Control, and Monitoring
- Vulnerability assessment, Incident Reporting, and Response
- Change Management and Recovery Plans
- Information Protection and Training
HVDC/FACTS Cyber security implementation
Cyber security fundamentals and best practices specifically for HVDC/FACTS are identified and different implementation options to achieve these best practices are examined along with their corresponding capital and operational cost considerations. The HVDC/FACTS specific best practises arranged to align with common global key cyber asset requirements are as follows:
Cyber asset risk assessment, classification, and identification:
- Risk assessments should be done on a periodic basis;
- Risk assessments should align with the transmission or reactive power support capacity contingency planning requirements and these requirements should strongly influence the segmentation of the network architecture;
- Cyber asset inventories should be organized based on the risk level of the assets;
- Risk assessment of cyber asset procurement and supply chain should be considered to protect against embedded malicious code or backdoors;
- Owner technical specifications need to be explicit about their risk requirements from the Owner's perspective as opposed to simply requesting compliance to standards only.
Physical security requirements, access control, and monitoring:
- Physical security segregation of HVDC/FACTS cyber assets should be determined by the required risk assessment considering N-1 contingency and availability requirements as per Figure 1;
- Areas of physical security segregation should be access controlled and monitored.
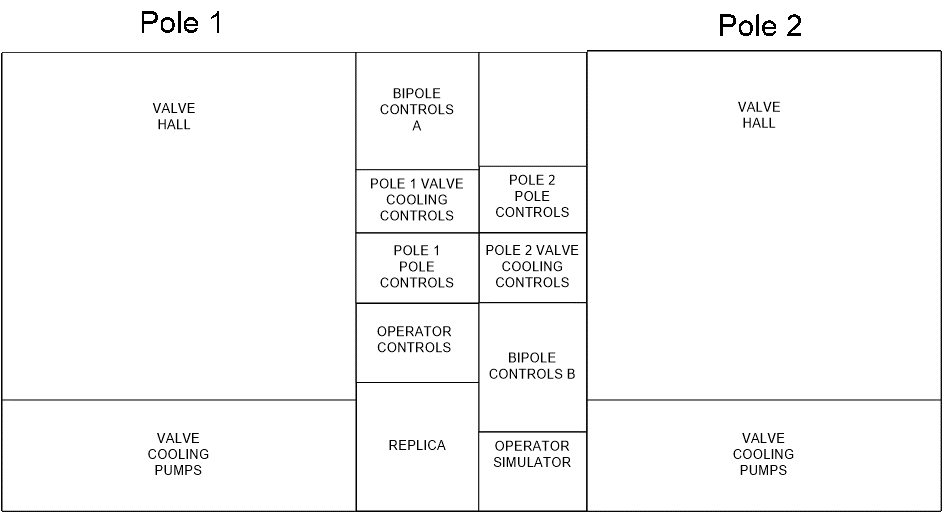
Figure 1 - Example of Physical Separation of Cyber Assets
Electronic security requirements, access control, and monitoring:
- Electronic security segregation of HVDC/FACTS system should be determined by the required risk assessment considering N-1 contingency and availability requirements as per Figure 2
- Areas of electronic security segregation should be access controlled and monitored
- Electronic security segregation should be as simple as possible, with all required high speed controls being within the electronic boundary, and operational status information sent on a completely segregated and isolated system
- Physical and electronic security controls should be in place during commissioning and security and penetration tests should be part of acceptance testing protocols
- Owners and developers should examine the latest developments in supply chain cyber security requirements and factory malware testing standards.
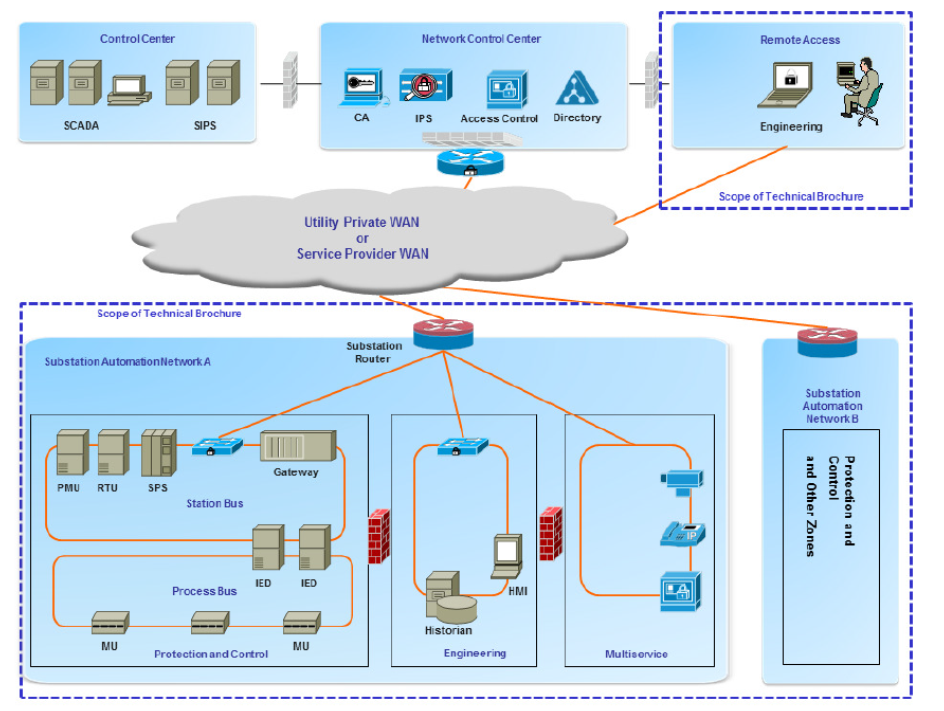
Figure 2 - Typical Electronic Separation for an AC substation
Vulnerability assessment and incident reporting and response:
- Owners should request and evaluate HVDC/FACTS vendors current vulnerability testing program in their design, procurement, manufacturing, and commissioning implementation;
- Specific and unique regional cyber incident reporting requirements should be clearly identified in the technical specification.
Change management and recovery plans:
- Formal change management program with full version and revision tracking is in place during Factory Acceptance Testing and during commissioning of HVDC/FACTS systems as a mandatory and auditable requirement;
- Controls simulators are used for testing and implementation of software changes/patches and formulation/training of recovery plans.
HVDC/FACTS Cyber asset lifecycle and responsibilities
The Brochure examines the HVDC/FACTS main circuit equipment and cyber asset lifecycles and their interdependence. This helps the reader to understand key lifecycle considerations for HVDC/FACTS cyber assets, lifecycle replacement plans and design requirements and to optimally achieve the best practices recommend in this Technical Brochure. Following HVDC/FACTS cyber asset requirements guidelines would facilitate successful replacement of cyber assets and should therefore be incorporated into a technical specification:
- Electronic security segregation should be as simple as possible, with all required high-speed controls being within the electronic boundary, and operational status information sent on a completely segregated and isolated system. Ideally, only discrete digital and analog signals are exchanged between a HVDC/FACTS control and protection system and a Windows based cyber asset such as an operator interface;
- Remote access requirements should be minimized and limited when possible. Ideally, only discrete digital and analog signals are exchanged between a HVDC/FACTS control and protection system and a Windows based cyber asset device such as routable interstation communication;
- The factory acceptance test scripts used to test the HVDC/FACTS control and protection system and a Windows based cyber asset in place during commissioning should be stored as part of the baseline configuration and version tracked so it can be used to commission replacement Windows based cyber assets;
- Owners should consider the purchase and use of replica control systems as per Figure 3, which would allow for integration testing of replacement of network devices in future and be used to test new devices, if upgrades/different manufacturer devices are chosen.
Consideration may be given to the use of “virtual machines” or non-Windows based operator interfaces to mitigate the cyber asset replacement lifecycle mismatch that exists today.
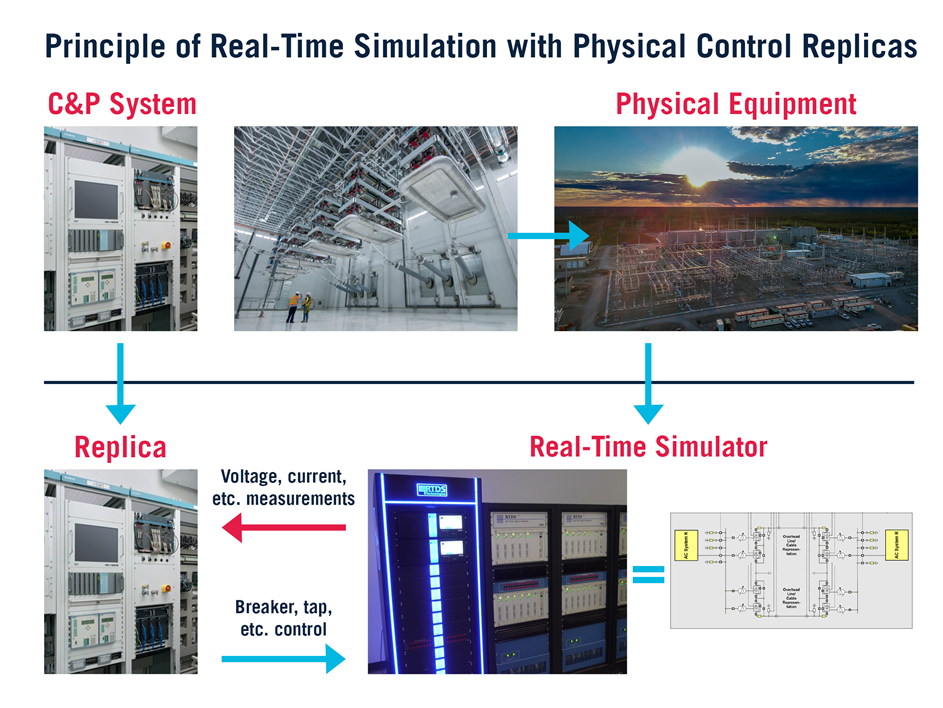
Figure 3 - HVDC Real-Time Simulator and Replica
HVDC/FACTS Cyber asset operational support
The Brochure examines the current requirements for operationally supporting HVDC/FACTS cyber assets. This includes resource, remote access, training, and vendor support options. This allows the reader to understand the operational support impacts that can influence overall lifecycle costs and technical specification requirements of HVDC/FACTS cyber assets. Operational and Maintenance guidelines were identified as follows:
- The owner and vendor need to agree on processes for patching, change management, incident response, and access controls that will be followed during design, manufacturing and commissioning as these are the processes that will be applied during operations;
- Owners should consider requirements that are applicable to all HVDC/FACTS projects, therefore, they can benefit from industry lessons learned and response to cyber threats;
- Owners should consider the use of replica control systems, which would allow for integration testing of replacement of network devices in future and be used to test new devices, if upgrades/different manufacturers’ devices are chosen;
- Remote access requirements should be minimized and limited when possible, and/or adequate operational budget and resources should be allocated for ongoing cyber security compliance;
- All cyber asset compliance activities should be demonstrated and tested during factory acceptance testing.
HVDC/FACTS Cyber asset technical specifications
The Brochure provides a technical specification guideline which incorporates HVDC/FACTs cyber asset best practices for the optimization of cyber security, asset replacement and operations & maintenance costs throughout the lifecycle of the assets. The proposed technical specification outline as follows:
- Applicable Regulations and Standards
- Cyber Asset Risk Assessment, Classification, and Identification
- Physical Security Requirements, Access Control, and Monitoring
- Electronic Security Requirements, Access Control, and Monitoring
- Vulnerability assessment, Incident Reporting, and Response
- Change Management and Recovery Plans
- Information Protection and Training
- Cyber Asset Replacement and Support Requirements
- Cyber Asset Operational & Maintenance Requirements
- Cyber Asset Supply Chain Requirements
- Cyber Asset Factory Testing Requirements
- Cyber Asset Commissioning Requirements
Additionally, important lifecycle cost considerations when formulating HVDC/FACTS technical specifications are discussed.
Conclusion
The Brochure has studied cyber security requirements globally and identifies best practices specifically for HVDC/FACTS applications. Best practices are provided for:
- Cyber Asset Risk Assessment, Classification, and Identification
- Electronic security requirements, access control, and monitoring
- Change management and recovery plans
- Cyber Asset Operational and Maintenance Guidelines
A proposed Technical Specification Outline is presented to attain these best practices and manage the other identified specific challenges of HVDC/FACTS Cyber Assets. As the technology of cyber security advance at a quick pace, the Brochure recommends being updated periodically, possibly every 3 to 5 years.


